
BitSiegeCTF Writeups
This past weekend, I had some time to spare and decided to attempt some of the challenges from the BitSiege CTF. The CTF had some interesting challenges which I enjoyed solving and even managed to get first blood and only solve for one of the challenges. This blog post is a walkthrough of some of the challenges.
Read More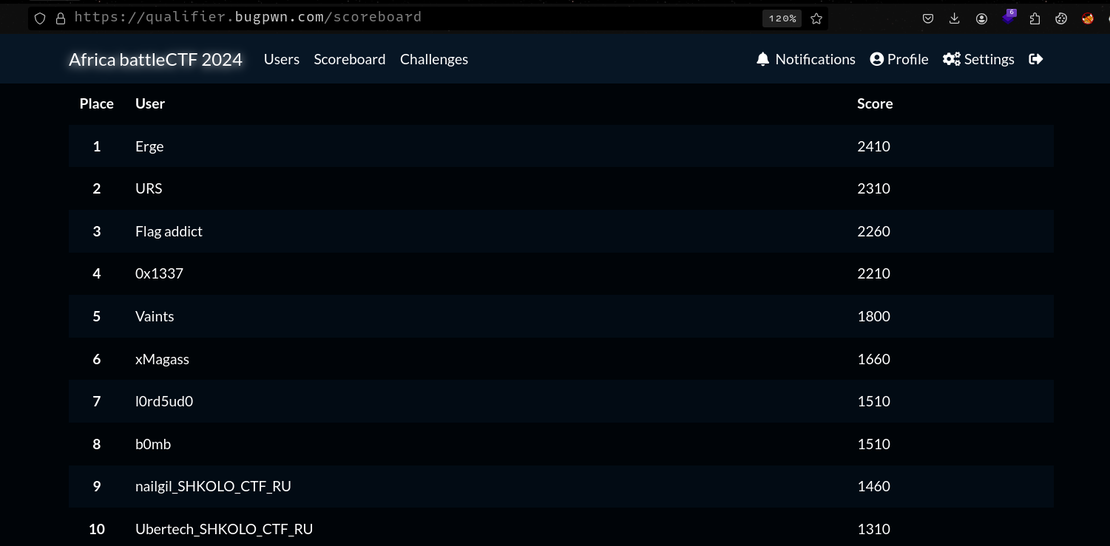
Africa Bug Pwn 2024 Writeups
Recently I took part in the Africa Bug Pwn 2024 Capture the Flag Competition and managed to get second position with 2310 points. The CTF was very interesting and I got to learn a thing or two. This blog post will be a writeup of some of the challenges I managed to solve.
Read More
ImaginaryCTF Argv Pwn Writeup
This blog post is a walkthrough of an interesting pwn challenge I came across in the imaginary ctf discord challenge.
Read More